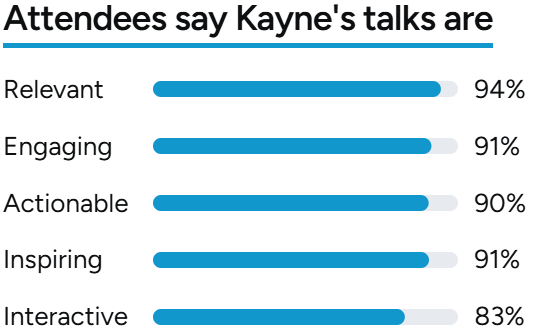
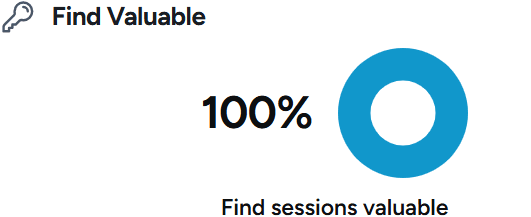
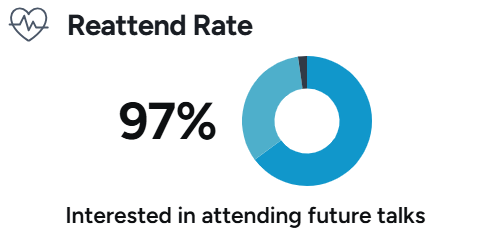
Speaking Topics
Bridging Cybersecurity and Business Risk
Cybersecurity risks are business risks. I frequently explore how organizations can align cybersecurity strategies with business objectives, enabling executives and boards to make informed decisions. Attendees will gain practical insights into how CISOs serve as a critical second line of defense and how compliance certifications can become a competitive advantage in regulated industries.
Navigating the Challenges of Compliance
Compliance isn’t just about meeting requirements; it’s about building trust. I share actionable steps to improve GRC maturity using my GRC Maturity Model and offer strategies to overcome the hurdles of passing audits and managing evidence requests. This session highlights practical ways to de-conflict relationships between cybersecurity and internal audit teams, fostering collaboration and efficiency.
Preparing for the Future of Regulation
The regulatory landscape is evolving, with AI and cybersecurity laws reshaping industries. In this session, I discuss horizon scanning techniques and how to adapt to emerging laws like the SEC’s cybersecurity disclosure rules or the EU AI Act. Attendees will leave with a clear understanding of how to align their strategies with global regulatory changes and litigation trends.
About Kayne

I’m Kayne McGladrey, keynote speaker, CISSP, the Field CISO for Hyperproof, senior IEEE member, and author of the GRC Maturity Model. With nearly three decades of experience in cybersecurity, I specialize in helping organizations navigate the intersection of governance, risk, and compliance (GRC) to build more secure and resilient businesses.
My work focuses on enabling CISOs, internal audit teams, and executives to align cybersecurity and business goals, communicate effectively with boards, and proactively address evolving global regulations. As a recognized thought leader, I’ve been spoken at events like Gartner IT Security & Risk, RSA, ISACA GRC, and the ISC2 Congress. My presentations are nuanced, accessible, and actionable, offering attendees practical guidance on current cybersecurity challenges and opportunities.
Throughout my career, I’ve advised Fortune 500 and Global 1000 companies, leveraging my ability to bridge the gap between business and technology. I’m passionate about reducing organizational friction, improving GRC maturity, and inspiring underrepresented communities to pursue cybersecurity careers.
Recent Articles and Media
AI, Business Risk & Threat Management: a CISO’s guide
This week’s special guest Kayne McGladrey, (blog: kaynemcgladrey.com ), CISO-in-Residence at Hyperproof, outlines the business challenges that CISO’s face, as we discuss new types of risk in daily threat management.
Understanding CMMC It’s a Process, Not a Project
“ If a manufacturing strategy can be exfiltrated from even one part of the supply chain it gives enemies an inside look at how equipment works. If they leverage that knowledge, warfighter lives are at risk. ”
Kayne McGladrey
Cybersecurity Influencers & Experts 2025: The Ultimate AI-Powered Guide
Winner of one of the top 50+ Cybersecurity Influencers to Follow in 2025
Testimonials
He explains technical problems in a high level manner anyone can understand. (see talk report)
Cody C.
The topic covered is something that every security person should know how to do and be aware of. This is what helps us justify our team, tools, and growth. (see talk report)
Evan Lund
Very inspiring and can help put cyber risks into terms that facilitate understanding for business folks. (see talk report)
Cao Chung
Very informative and important. What Kayne talked about is what needs to be talked about more. (see talk report)
Riley Maltos